AWS Releases an Overview of AWS Lambda’s Security
This PDF is a great read for any security minded folk who are trying to understand the humming of a serverless environment.
A very important thing to understand is the isolation model as defined here in this handy diagram from AWS:
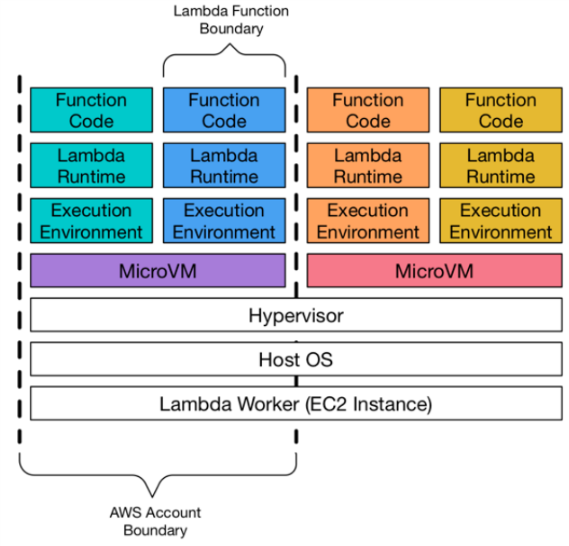
From the post:
Along with AWS proprietary isolation technologies, these mechanisms provide strong isolation between execution environments. This isolation ensures that environments are not able to access or modify data that belongs to other environments. Although multiple execution environments from a single AWS account can run on a single microVM, microVMs are never shared or reused between AWS accounts. At this time, AWS Lambda uses two different mechanisms for isolating microVMs: EC2 instances and Firecracker. EC2 instances have been used for Lambda guest isolation since 2015. Firecracker is a new open source hypervisor developed by AWS especially for serverless workloads, and was introduced in 2018. The underlying physical hardware running microVMs will be shared by workloads from multiple accounts.
If you’re new to Firecracker then check out this handy blog post from AWS: https://aws.amazon.com/blogs/aws/firecracker-lightweight-virtualization-for-serverless-computing/
The PDF / White Paper covers the following areas an is worth the read:
- Lambda Runtime Environment
- Isolation Between Functions and Between MicroVMs
- Storage and State
- Invoke Data Path
- Runtime Maintenance in Lambda
- Monitoring and Auditing Lambda Functions
- Amazon CloudWatch
- Amazon CloudTrail
- AWS X-Ray
- AWS Config
- Architecting and Operating Lambda Functions
- Lambda and Compliance


You must be logged in to post a comment.