AWS Vendor Role Management
Hi,
At some point you may have a vendor managing your AWS environment.
The vendor may have their own requirement to have the AWS env created on “their account”. As such they own the IAM Root account.
It is possible that they have decided to use a standard for this, and that their standard may include a secondary global administrator account.
I recommend requesting they cloud form this account for security reasons.
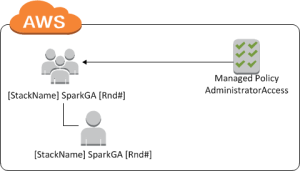
Cloud formation will add the stack name and a random number to the entities it creates in AWS.
There is no way around this.
So when you create an IAM User the account will be formated:
[STACKNAME][ACCOUNTNAMEYOUUSED][RANDOMNUMBER]
e.g: PaulsStackGlobalAdminA341201
Some people don’t like this. However consider the fact that this makes a unique account each time the formation is run. Therefore any vendor being forced to use this will be ensuring your environment cannot be hacked by anyone knowing a “Standard” from that vendor. Some vendors are also sloppy with password management eh.
I recommend that this is hooked into the AWS Managed Policy for AdministratorAccess.
The cloudformation view is this:
For additional users and roles, one will likely require a normal naming convention. To do this I recommend using the AWSCLI in a batch way and will blog about this in another post soon.
